What is Cysic (CYS)?
What Is Cysic?

(Source: cysic_xyz)
Cysic is a decentralized computing infrastructure built on the ComputeFi vision, designed to transform GPUs, ASIC miners, and servers into programmable, verifiable, and liquid resources. Cysic’s mission is to make computation a public resource, not a privilege, unlocking computational assets that are liquid, programmable, and verifiable. Just as DeFi unlocked capital, ComputeFi unlocks computational resources previously locked within closed platforms.
ComputeFi: Financializing Computation
ComputeFi is the core concept introduced by Cysic, turning GPUs, ASICs, and other accelerators into a globally accessible marketplace. On ComputeFi, users can transparently request, execute, and verify all types of computational tasks—from ZK proofs to AI inference to crypto mining.
Why Is ComputeFi Necessary?
Over the past decade, digital resources like finance, storage, and bandwidth have gradually decentralized, but computation remains highly concentrated. Cloud giants such as AWS, Google Cloud, and Azure dominate the AI computing market. Mining has become heavily industrialized, zero-knowledge proof networks are still experimental, and the AI compute market is highly fragmented.
Unlike storage or bandwidth, computation is inherently complex. Training large language models (LLMs), generating zkSNARK proofs, and mining Bitcoin blocks each require distinct hardware, software, and verification logic. This complexity explains why a universal computation market has yet to emerge.
Core Features of ComputeFi
- Programmable: Like capital composability in DeFi, ComputeFi enables composable computation through APIs and workflows.
- Verifiable: Computational results must be validated by cryptographic proofs, redundant computation, or consensus mechanisms.
- Liquid: GPU hours, ASIC hash rates, and ZK proofs can be traded across domains.
- Accessible: Whether you’re an AI lab or a student with a gaming PC, you can request or provide computation.
Cysic unlocks computation from closed resources, building a decentralized computational economy.
Cysic Network: Roles and Mechanisms
Cysic Network brings together different participants in a decentralized ecosystem, forming the ComputeFi ecosystem. The main roles include:
- Compute Providers: Ranging from individual GPUs to industrial ASIC clusters, these participants supply computational resources, receive tasks, and return results.
- Task Requesters: dApps, enterprises, or users needing computation, such as rollup operators, zkVM proof networks, or crypto mining pools.
- Verifiers: Independently check computational results for correctness, using redundant computation or cryptographic methods.
- Marketplace: The ComputeFi coordination layer matches tasks with providers, balancing performance, fairness, and reliability.
For example, in a ZK proof workflow: the requester submits task requirements and rewards, providers bid for the task, and once completed, verifiers inspect the results. Rewards are then distributed to providers and verifiers, with the entire process recorded on the Cysic Network blockchain.
In ComputeFi, computational resources are measured in workload units:
- GPU computation is measured in FLOPs
- ASIC computation is measured in hash rate
- Proof computation is measured in zkVM cycles
The protocol standardizes heterogeneous resources, enabling fair pricing, allocation, and trading.
System Architecture and Security
Cysic Network is built with Cosmos CDK as a Layer-1 blockchain and uses the CometBFT consensus mechanism, which maintains network integrity even if up to one-third of nodes are malicious or faulty. Its Proof-of-Compute consensus mechanism considers both token staking and computational participation in consensus.
The network architecture has four layers:
- Hardware Layer: CPU/GPU/FPGA servers, mining devices, and mobile devices
- Consensus Layer: CometBFT BFT consensus, ensuring security and fault tolerance
- Execution Layer: Handles task scheduling, job routing, bridging, and voting, implemented through EVM smart contracts
- Product Layer: User-facing product interfaces, including ZK proof marketplaces, AI inference frameworks, and crypto mining platforms
This modular architecture allows each layer to be upgraded independently, supports rapid integration of new proof systems and AI models, and provides clear interfaces for developers and hardware providers.
Hardware and Protocol Co-Design
Cysic’s main competitive advantage is its vertical integration of hardware and protocol:
- ZK ASIC: Specialized ASICs boost zero-knowledge proof throughput and energy efficiency, supporting real-time block proofs on Ethereum.
- GPU Clusters: Optimized for AI inference and training, delivering high throughput and trusted execution.
- Portable Miners: Low-power Dogecoin/Bitcoin miners, easy to connect to the network, encouraging retail participation.
- Heterogeneous Resource Support: Beyond proprietary hardware, supports commercial GPUs and HPC clusters, ensuring global participation and decentralization.
Hardware and protocol co-design anchors ComputeFi’s supply in deployable, real-world infrastructure.
Use Cases and Examples
ComputeFi is applicable across industries and use cases:
- AI Market: Deploy models on demand, pay for inference, and have verifiers ensure result accuracy.
- Blockchain Infrastructure: Rollups and privacy chains can outsource ZK proof computation, sharing revenue with providers.
- Mining Integration: Traditional mining power can serve as ComputeFi liquidity, enabling flexible switching to AI or ZK tasks.
- Scientific HPC: Offers cost-effective, verifiable computation for research, including genomics and climate modeling.
Examples include:
- Ethereum Block Proofs: Globally distributed providers share proof workloads, reducing latency and costs.
- Verifiable AI Inference: Users pay only for correct outputs, enabling decentralized AI APIs.
- Dogecoin Mining Integration: Retail miners participate in ComputeFi, expanding decentralization and grassroots adoption.
Tokenomics
Cysic adopts a dual-token model: $CYS and $CGT.
- $CYS: The native token, used for transaction fees, block rewards, and network activities, sustaining network vitality.
- $CGT: The governance token, acquired by staking $CYS 1:1, used for governance and compute pool management. The unstaking period is longer than the staking period.
Token Distribution
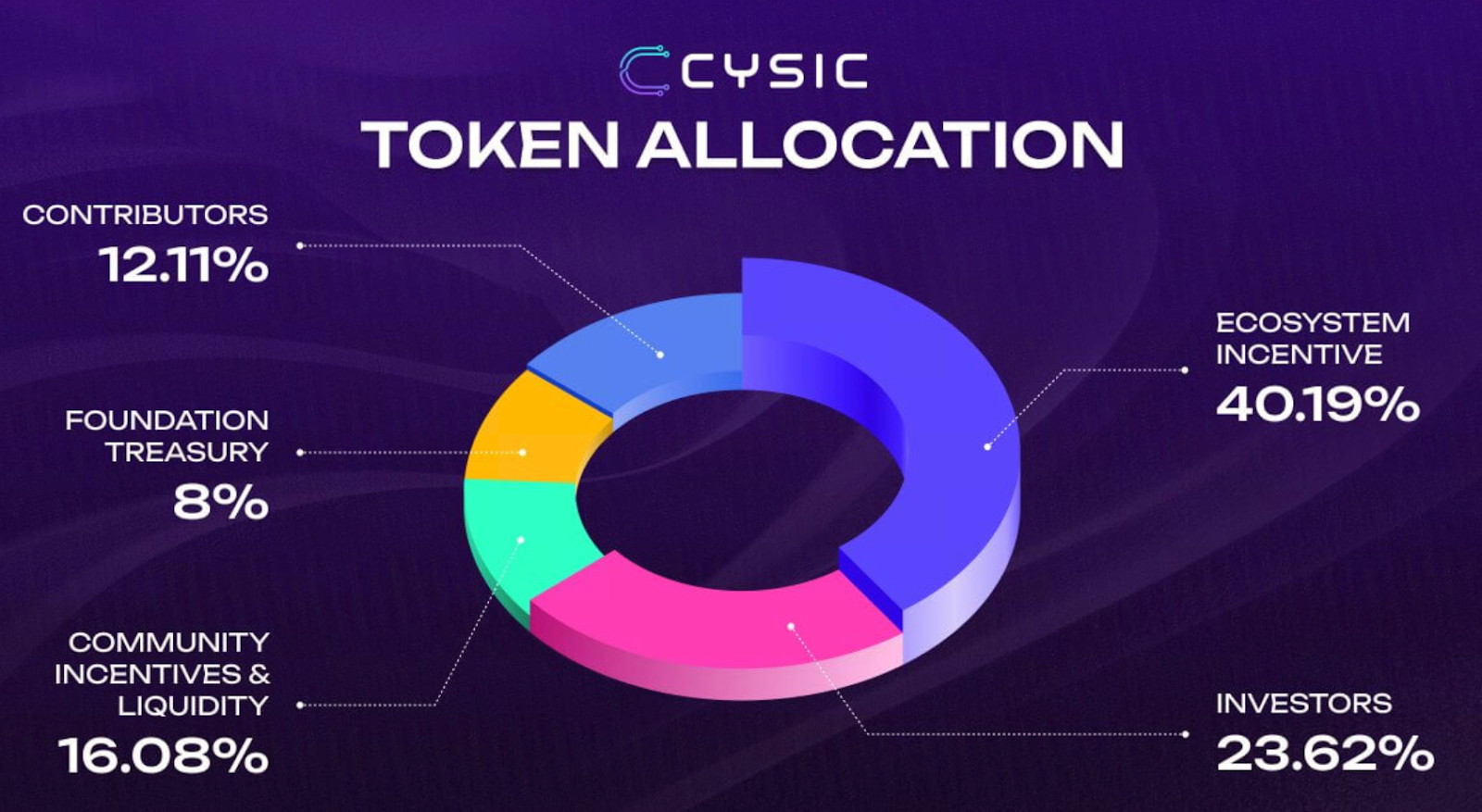
Total supply: 1 billion $CYS (fixed, no inflation):
- Ecosystem Incentives 40.19%: Dynamic grants, rewards, mining rewards, and staking incentives, gradually transitioned to DAO control.
- Investors 23.62%: Seed and Series A supporters, 12-month lockup plus 12-month linear release.
- Contributors 12.11%: Core team allocation, 12-month lockup plus 36-month linear release.
- Community Incentives and Liquidity 16.08%: Testnet participants, NFT activity rewards, governance airdrops, and initial liquidity provision.
- Foundation Treasury 8%: Protocol operations, research, and upgrades, 12-month lockup plus 24-month linear release, controlled by DAO.
(Source: Cysic)
This token model incentivizes compute providers, verifiers, and community participation, establishing a self-sustaining, decentralized network economy.
To learn more about Web3, click to register: https://www.gate.com/
Summary
Computation has become the most critical resource in the digital era, yet it remains dominated by a few cloud providers and industrial mining pools. Cysic, through ComputeFi, transforms GPUs, ASICs, and accelerators into a programmable, verifiable, and liquid global market, breaking computational silos and unifying ZK proofs, AI inference, mining, and HPC workloads. Its modular architecture ensures scalability, while vertical integration of hardware and protocol delivers real-world utility. ComputeFi is not just a service—it’s an asset, accessible to anyone, anywhere. Cysic is building the next-generation Web3 computing foundation, empowering the future of AI, crypto, and scientific research.
Related Articles

2025 BTC Price Prediction: BTC Trend Forecast Based on Technical and Macroeconomic Data

Flare Crypto Explained: What Is Flare Network and Why It Matters in 2025

Pi Coin Transaction Guide: How to Transfer to Gate.com

How to Use a Crypto Whale Tracker: Top Tool Recommendation for 2025 to Follow Whale Moves

What is N2: An AI-Driven Layer 2 Solution
